Course Overview
Is This Course For You?
- You understand basic AWS services like IAM, EC2, and S3
- You want to learn real-world AWS cloud pentesting, not just theory
- You’re a pentester, red teamer, or security professional expanding into cloud
- You want hands-on labs covering IAM abuse, misconfigurations, SSRF, and privilege escalation
- You want skills that actually translate to real AWS attack paths
- You are completely new to cloud concepts
- You’re looking for an AWS fundamentals or certification-only course
- You want a purely blue-team or SOC-focused cloud security course
- You prefer theory and videos over hands-on exploitation
- You want shortcuts without understanding real cloud attack tradecraft
Prerequisites
- Basic Linux Knowledge
- Basic Pentesting & Security Concepts
- Basic Command Line Skills
Course Curriculum
AWS Pentesting Course
138 Learning Materials
Module 1: AWS & AWS Pentesting
Intro to AWS Pentesting Course
Accessing Labs
Overview of AWS
Cyber Kill Chain (Cloud)
What is AWS Pentesting
Initial Access Scenarios
Real World Case Studies
Module 2: Learning AWS Basics - A Practical Approach
AWS Basics
AWS Account
AWS Architecture
Practical - A look at an AWS Account
Practical - Creating a User
Practical - Giving Permssion to a User
Practical - Creating your first EC2 Instance
Practical - Creating your first S3 Bucket
Practical - Setting up MFA
Module 3: Deep Dive into IAM Service
Understanding IAM Service
IAM Identities
Taking a deep dive into Roles
Practical - Role Usage (Service to Service)
Practical - Role Usage (Account to Account)
Role Usage (External ID to Service)
IAM Access Keys
Practical - Solving your first Lab
Practical - Automating the Enumeration with aws-enumerator
Understanding ARN
Module 4: Understanding different types of IAM Policies
Types of Policies in IAM
IAM Identity Permission Policy
Practical - IAM Identity Permission Policy
Few More Examples
Types of IAM Identity Permission Policy
Practical - IAM Identity Permission Policy
Resource Based Policy
Bucket Resource Policy
Bucket Resource Policy - Examples
Practical - Bucket Resource Policy
Trust Policy
Permission Boundary
Practical - Permission Boundary
Session Policies
Practical - Session Policies
Module 5: AWS Organizations and their policy types
AWS Organizations
Practical - AWS Organizations
Service Control Policies
Practical - Service Control Policies
Resource Control Policies
Practical - Resource Control Policies
Policy Evaluation Logic
Module 6: Common IAM Misconfigurations
Misconfiguration 1 - Wildcard Everywhere
Misconfiguration 2 - Inline Privileged Policy
Misconfiguration 3 - Over-Permissive Trust Policy
Misconfiguration 4 - Over-Permissive Resource Based Policy
Maybe a Misconfiguration 5 - KMS Key Policy
Misconfiguration 6 - NotAction or NotResource
Module 7: IAM Initial Access
Practical - Account ID Manual Enumeration (Public Buckets)
Practical - Account ID Automated Enumeration (Public Buckets)
Practical - Account ID Enumeration (AMIs and Snapshots)
Practical - Manual Enumeration of Users and Roles
Practical - Automated Enumeration of Users and Roles (Pacu)
Practical - Initial Access - Weak Credential in Use
Module 8: IAM Enumeration
Enumeration Basics
Practical - General Enumeration
Practical - User Enumeration
Practical - Group Enumeration
Practical - Role Enumeration
Practical - Policy Enumeration
Service Enumeration
Module 9: IAM Exploitation & Privilege Escalation & Persistence
Practical - Change Group Membership
Practical - Creating a New Policy Version
Setting the Default Policy Version
Creating User Access Key
Creating a New Login Profile
Updating an Existing Login Profile
Attaching a Policy (User, Group & Role)
Creating/Updating an Inline Policy (User, Group & Role)
Updating the AssumeRolePolicyDocument of a Role
IAM Persistence
Module 10: STS & KMS Service
STS Basics & Misconfiguration
KMS Basics & Practical
Enumerating & Finding Misconfigurations
Module 11: SecretsManager Service & SSM Parameter Store
SecretsManager Basics and Enumerating Secrets
SSM Parameter Store Basics and Enumerating Parameters
Module 12: EC2 Service
EC2 Basics & Practical
Initial Access & Enumeration
Practical 1 - Exploitation & Priv Esc
Practical 2 - Exploitation & Priv Esc
Few More Exploitation & Priv Esc
Module 13: S3 Service
S3 Basics & Practical
Real World Case Studies
Initial Access, Enumeration & Exploitation
Practical - Initial Access, Enumeration & Exploitation
Module 14: Lambda Service
Lambda Basics
Practical - Creating your first lambda Function
Practical - Creating your second lambda fucntion
Practical - Lambda Enumeration
Practical - Lambda Exploitation 1
Practical - Lambda Exploitation 2
Creating a Serverless Application
Module 15: API Gateway
API Gateway Basics
Practical - Creating a vulnerable API Gateway and Exploiting it
Practical - Exploiting API keys
API Gateway Authorizers
Practical - Lambda Authorizer
AWS IAM Authorizer
Cognito User pool Authorizer
Practical - API Gateway Enumeration
Module 16: Cognito
Cognito
Cognito User pools
Practical - Creating your first User Pool
Cognito Identity pool
Practical - Creating your first Identity Pool
Practical - Exploiting Unauthenticated (Guest) Identity pool
Practical - Exploiting Self Registration Feature
Practical - Exploiting Custom Attributes
Practical - Cognito Enumeration
Module 17: DynamoDB
DynamoDB Basics
Creating your first DynamoDB Table
Module 18: IAM Identity Center
IAM Identity Center Basics
Practical - IAM Identity Center
Practical - Enumerating IAM Identity Center
Module 19: CloudTrail
CloudTrail Basics
Practical - Creating your first Trail
Practical - Analyzing the logs
Bypassing CloudTrail Logging
Module 20: GuardDuty
GuardDuty Basics
Enumerating & Bypassing GuardDuty
Module 21: AWS Pentest Tools
Boto3
ScoutSuite
Prowler
PMapper
Cloudsplaining
Cloudfox
Pacu
Module 22: Report Writing & CAPT Exam
Report Writing
CAPT Exam
Module 23: Course Resources
AWS Pentesting Course PPT
Commands & Scripts
Template Report
Course Instructor

Shashi Kant Prasad
Principal Security Consultant
Shashi Kant Prasad is a skilled red teamer at Redfox Security with expertise in Web, Cloud, Hardware, DevOps, and Red Teaming. He also trains peers at top security conferences.
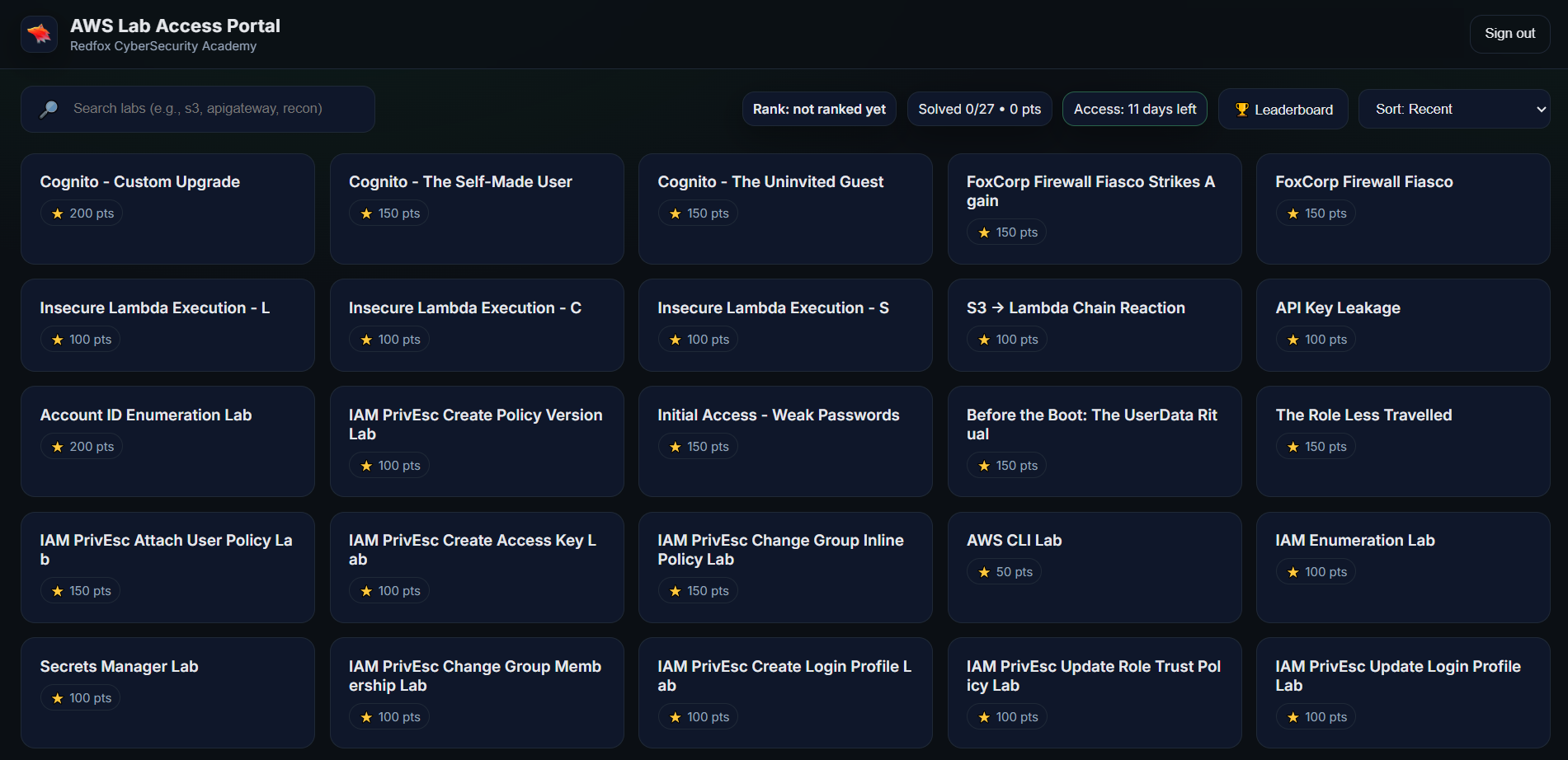
Lab Portal
Key Takeaways
- Life time access to course and resources.
- 30 days of free lab access.
- Private Discord community access for direct support and networking.
- One attempt at the Certified AWS Penetration Tester Exam (CAPT).
- A professionally structured report template is provided for use in real-world engagements.
Get Certified (CAPT)
Earn the Certified AWS Penetration Tester (CAPT) certification to validate your expertise in AWS exploitation, red teaming tactics, and cloud security bypass techniques. This certification proves your ability to conduct real-world attack simulations against AWS environments, making you a valuable asset in cloud security. Gain hands-on experience through labs and instructor-led training, preparing for roles like Red Teamer (Cloud) or Cloud Penetration Tester. Participants receive a CAPT certificate upon completing the bootcamp and passing the practical exam.

This is not a multiple-choice cert.
You earn it by exploiting real AWS environments under attack conditions.
Ready to Master the Art of Pentesting?
Affordable Price
Unlock your potential with affordable upskilling! Our unbeatable course prices are your chance to level up without breaking the bank.
Lifetime Access
Acquire lifetime access to our resources when you buy our courses. Gain knowledge today and unlock a lifetime of learning.
Certificate of Completion
Upon completing our course, you'll receive a certificate of completion to showcase your new skills. Add it to your resume or LinkedIn profile.
Hands-On Experience
Get hands-on experience with real-world scenarios and challenges, giving you practical skills that you can apply immediately in your career.
Expert Instructors
Learn from industry experts with years of experience in pentesting, who are passionate about sharing their knowledge and helping you succeed.
Flexible Learning
Whether you're a beginner or an experienced professional, our courses are designed to meet you where you are and help you reach your goals.
Get in Touch
Have a question, need assistance, or want to collaborate? We’re here to help!
Whether you're looking for cutting-edge cybersecurity solutions or expert training or want to learn more about our services, contact us today.
By clicking on Continue, I accept the Terms & Conditions,
Privacy Policy & Refund Policy